
Meet PIDGN
Powered by:


Base PIDGN Model

Lollipop For Scale
PIDGN developed by Grackle Labs; is a modern, plug-and-play red-teaming device that merges USB based pen-testing capabilities with a wireless (802.11) command hub—no external controller or physical interaction is required. Designed for red teamers and penetration testers, PIDGN emulates a USB keyboard to deliver customizable payloads while hosting a local command center over its own password protected Wi-Fi hotspot.
Once plugged in, it instantly appears as a keyboard and executes tailored scripts, enabling HID attacks, remote command execution, and post-exploitation actions. Its browser-based interface requires no apps or pairing—just connect to the password protected hotspot and launch. Payloads can be created, sorted by established OWASP pen-testing phase, and dynamically updated with variables like C2 addresses, making PIDGN a compact, field-ready tool for on-the-fly operations.
PIDGN Defcon Pre-Release Order (Alert)
.jpeg)
$ 115.00 USD
PIDGN developed by Grackle Labs; is a modern, plug-and-play red-teaming device that merges USB based pen-testing capabilities with a wireless (802.11) command hub—no external controller or physical interaction is required. Designed for red teamers and penetration testers, PIDGN emulates a USB keyboard to deliver customizable payloads while hosting a local command center over its own password protected Wi-Fi hotspot. This is a unique pre-release offered for Defcon 33 - Pick-up direct in Las Vegas.
PIDGN Defcon Pre-Release Order (Electric)
%20Large.png)
$ 115.00 USD
PIDGN developed by Grackle Labs; is a modern, plug-and-play red-teaming device that merges USB based pen-testing capabilities with a wireless (802.11) command hub—no external controller or physical interaction is required. Designed for red teamers and penetration testers, PIDGN emulates a USB keyboard to deliver customizable payloads while hosting a local command center over its own password protected Wi-Fi hotspot. This is a unique pre-release offered for Defcon 33 - Pick-up direct in Las Vegas.
PIDGN Defcon Pre-Release Order (Black)
%20Large.png)
$ 100.00 USD
PIDGN developed by Grackle Labs; is a modern, plug-and-play red-teaming device that merges USB based pen-testing capabilities with a wireless (802.11) command hub—no external controller or physical interaction is required. Designed for red teamers and penetration testers, PIDGN emulates a USB keyboard to deliver customizable payloads while hosting a local command center over its own password protected Wi-Fi hotspot. This is a unique pre-release offered for Defcon 33 - Pick-up direct in Las Vegas.
PIDGN - Black

$ 100.00 USD
PIDGN is a stealthy, plug-and-play red teaming device that merges USB attack capabilities with a wireless command hub—no external controller or physical interaction required. Designed for red teamers and penetration testers, PIDGN emulates a USB keyboard to deliver customizable payloads while hosting a local command center over its own password protected Wi-Fi hotspot.
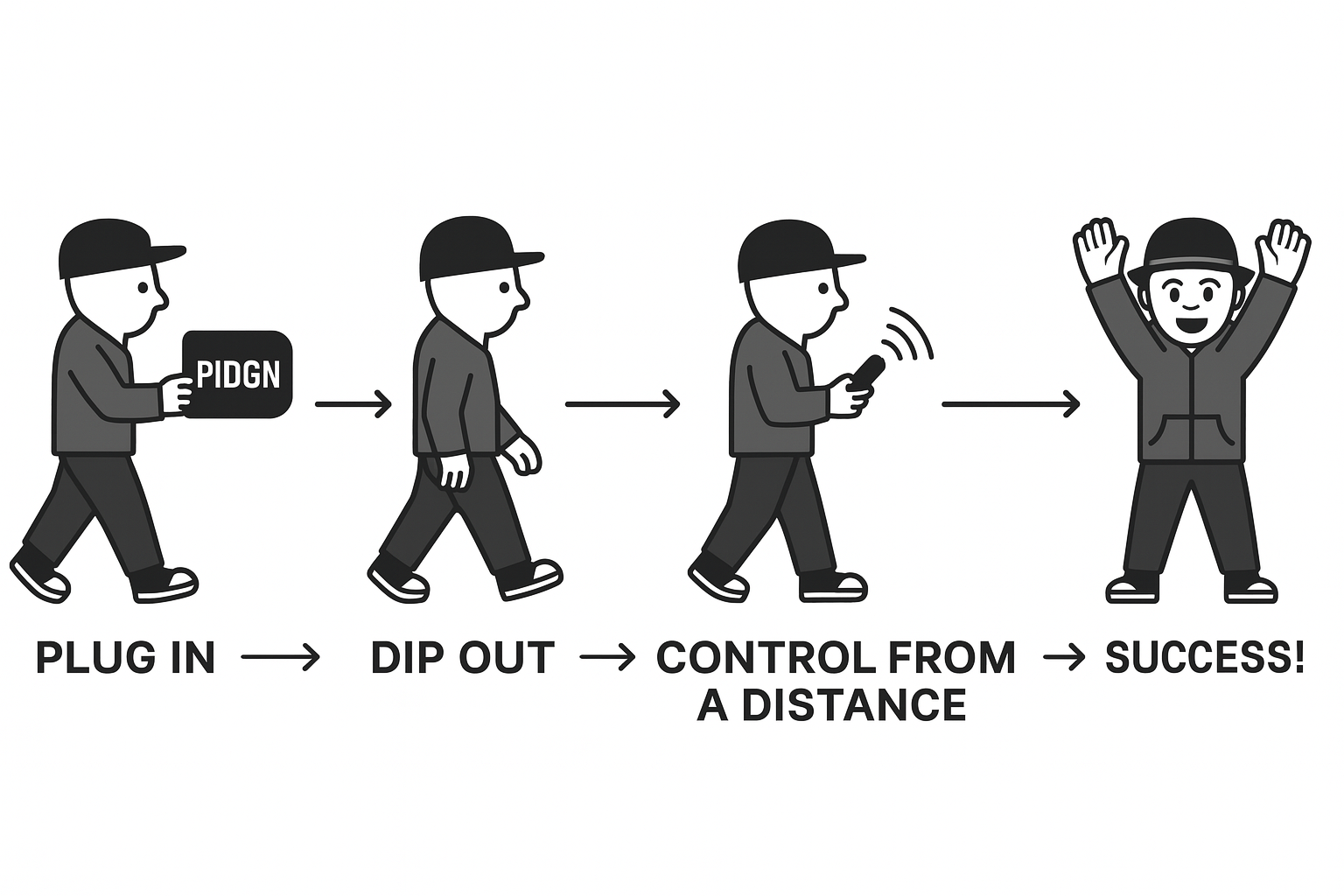

Control From 300+ Feet Away
Capability Overview
Preloaded with Scripts for Every Phase of the Pen-Testing Methodology
PIDGN comes preloaded with a full suite of scripts aligned with every phase of the pen-testing methodology, allowing penetration testers to act fast, pivot intelligently, and maintain momentum during assessments.
Whether you're conducting recon, delivering payloads, or establishing persistence, PIDGN has pre-programmed routines ready to deploy at the push of a button, allowing you to get remote instance feedback via the remote interactive interface. Once plugged in, it instantly appears as a keyboard and executes tailored scripts, enabling HID attacks, remote command execution, and post-exploitation actions. Its interactive remote browser-based interface requires no custom apps or pairing—just connect to the password protected hotspot and launch your web browse of choice. Payloads can be created, sorted by pen-testing phase, with the ability to dynamically update various variables to match the environment being reviewed.
Additionally, custom paylods can be developed using the PIDGN scripting platform making PIDGN a compact, field-ready tool for on-the-fly operations.
Included Phases & Capabilities:
Recon: Initiate scripts for tasks such as system identification, domain enumeration, and basic environment mapping.
Scanning: Launch targeted scans for open ports, live hosts, and exposed services across the network.
Exploitation: Deploy pre-configured payloads to exploit discovered vulnerabilities and gain initial access.
Privilege Escalation: Execute routines to escalate access rights, harvest tokens, or bypass UAC restrictions.
Lateral Movement: Utilize built-in tools to move through the network, dump credentials, or reuse sessions.
Post Exploitation: Run cleanup scripts, establish persistence, or exfiltrate key data via your configured C2.
PIDGN which empowers testers with turnkey, on-demand payloads that reduce time spent typing and maximize time spent testing and reporting.
Core Features:
Plug-and-Play USB HID Emulation: Acts as a keyboard to send keystrokes to the host machine Compatible with Windows and Linux.
Wi-Fi Access Point Mode: Broadcasts its own hotspot (default SSID: Pigeon) No internet required for use.
On-Device Web Interface: Hosted server with HTML interface (accessible via http://192.168.4.1) Works on mobile and desktop browsers.
Modular Payload System: Locally stored payloads organized by OS and/or testing phase.
Web Interface Capabilities Command Execution: Execute predefined payloads via links. PIDGN also supports custom payload input via text input on the Custom tab.
Custom Scripting Support: Input raw payload lines (e.g., WIN+R, notepad, ENTER) which are sent live from your phone to execute on the target machines.
Live Output Rendering: Displays command line output after script executionUsed to show status, results, or error messages.
Settings Management: Update IP/Port for C2 communications, and SSID settings via the web interface.
Command Cheat Sheet: Quick reference for supported keystrokes and variables built into the server, no need for external research.
Stealth and Secure No Installation Required on Target Host: Executes payloads without leaving artifacts (unless intended).
Encrypted Payload Transfer (planned): Future support for AES-encrypted payload definitions.
Offline Usage: Device operates independently without external servers or external Internet source.
Scripting: PIDGN uses a lightweight scripting language designed for rapid offensive operations. It's based on simple, human-readable commands similar to batch scripting and keystroke injection syntax. You could call the language Batch+. Each line in a script represents a specific action—such as launching an app, typing text, or executing key combos—making it easy for both beginners and pros to write and modify payloads on the fly.
No coding experience? No problem. If you can type, you can script with PIDGN.
Devevloped on a light-weight energy efficient ESP-32 board.
High-Performance ESP32-S3 Microcontroller: The Arduino ESP32 is powered by the ESP32-S3 chip, running at 240 MHz.
Wi-Fi & Bluetooth 5.0 Connectivity: Equipped with Wi-Fi 802.11 b/g/n, and Bluetooth 5.0, the ESP32 provides reliable and fast wireless communication.
Modern USB-C Port: The USB-C port ensures faster programming, more efficient power delivery, and improved connection stability, making the ESP32 easier to work with for both prototyping and production stages. The ESP32 comes with your choice of USB or UART modes.
HID Support for Custom Input Devices: The board supports Human Interface Device (HID) profiles, enabling you to create custom devices like keyboards, mice, and other input peripherals. Whether you're building a custom controller, USB-based interface, or remote input device, the ESP32 gives you the flexibility to develop innovative solutions.
MicroPython Compatibility: The Arduino ESP32 is compatible with MicroPython, offering an easy-to-use programming environment for rapid prototyping. This makes it ideal for developers who prefer Python for embedded applications, enabling interactive coding, quick testing, and faster iteration of IoT projects.

Under the hood